Phishing attacks are becoming more prevalent as a form of attack here in the Philippines. More SMS and email scams are being sent to individuals on a daily basis to try and steal credentials from those who are not familiar with it. It has become so prevalent that most Philippine banks have made many campaigns to warn their users how to spot a Phishing attack. Knowledge on these kinds of attacks is the best way to prevent them. We at CT Link are committed to helping spread awareness through cyber security tips that can help to spot fishy SMS or emails.
Cyber Security Tips on How to Spot a Phishing Attack
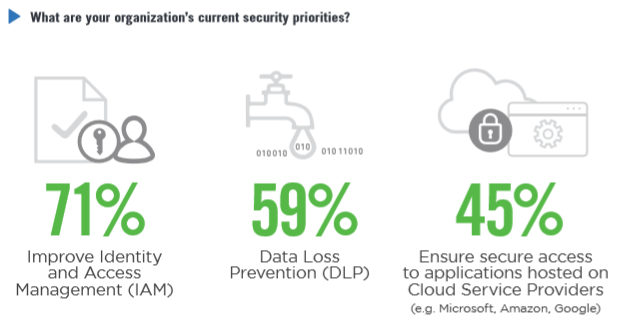
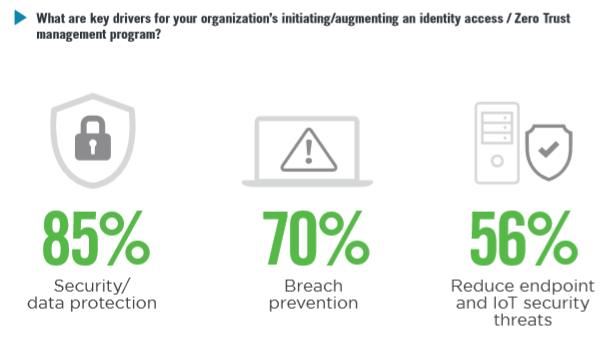
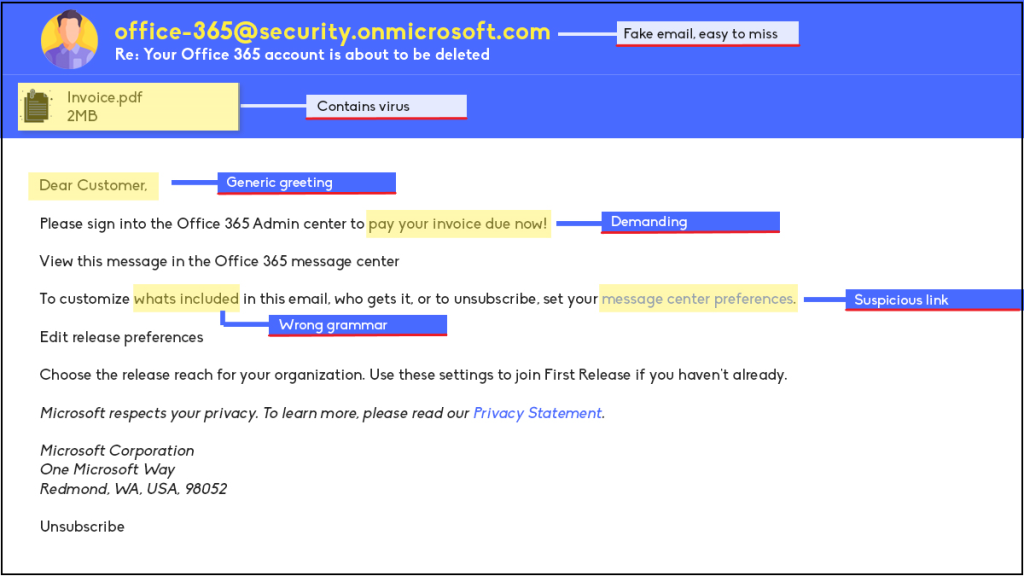
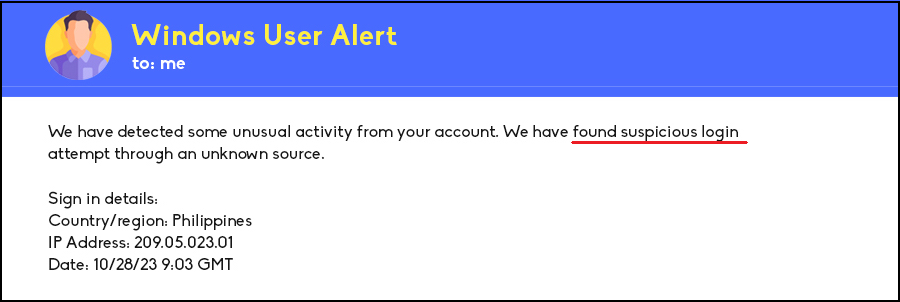
So what are simple ways to help spot a Phishing attack? Well from the example email example below, we can start looking from top to bottom.
- Check the email domain carefully – does it look legitimate? If you are unsure, you can easily look online to see if it is.
- Are there any attachments – Always be wary of attachments, never open files until you have confirmation the email is legitimate.
- Generic Greetings and Urgency – Emails from your legitimate accounts would not be refer you vaguely and would not push for immediate resolution of a problem.
- Wrong grammar or Typos – Emails are professionally made and proofread by bigger companies. If there are typos or bad grammar, it most likely a Phishing attack.
- Suspicious links – When it comes to links in an email, it is always best to never open until sure, or preview the link on a desktop if possible to see where its going.
For more examples and explanations, read further below as we go in better detail on what to look out for!
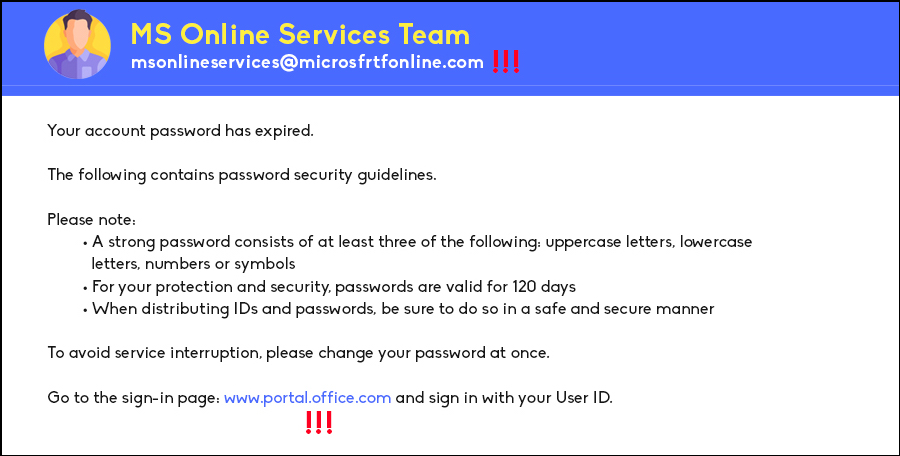
Examine the Sender’s Email Domain or Number
After reviewing the message, check the sender’s email or phone number. Legitimate companies typically use consistent and familiar domain names or phone numbers. If you notice personal numbers or typos in the email domain, or if it uses generic domains like Gmail or Yahoo, it’s likely a phishing attempt.
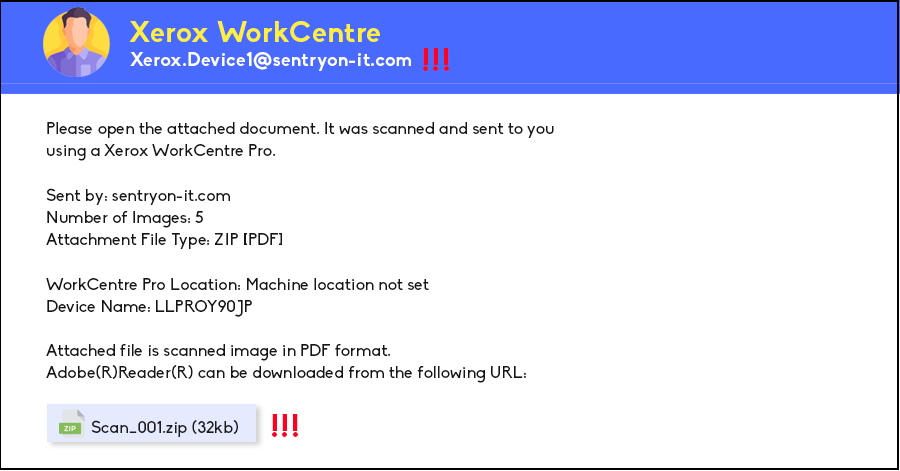
Beware of Links and Attachments
Another red flag is the presence of attachments or links in the email or SMS. Exercise caution when dealing with email attachments, and always verify their legitimacy before opening. Be especially wary of files with unfamiliar extensions, as these are commonly associated with malware (e.g., .zip, .exe, .scr). For links, hover your cursor over them to preview their destinations. It’s best practice to ask for confirmation before clicking any link.
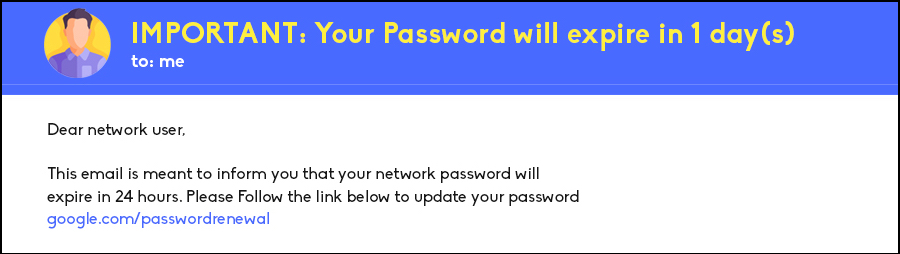
Be Cautious of Urgency in Messages
If you receive emails or SMS messages claiming that something urgent has occurred with your account, such as “your password has expired,” “unusual account activity,” or “response required,” exercise caution. These messages play on your fears to prompt immediate action. Take a moment to consider their authenticity.
Pay Attention to Message Content
If the email or message doesn’t address you by name or contain personal details, it’s likely fraudulent. Legitimate entities should have your information on hand. Additionally, watch for typos or grammatical errors in the message, as professionally crafted communications are carefully proofread. Scammers often rush or may not have English as their first language.
Cyber Security Tips: What to Do If You Suspect a Phishing Attack?
As mentioned earlier, it’s wise to consult your administrator or someone well-versed in security matters. You can also fact-check online to confirm the legitimacy of emails or SMS messages. Taking a moment to verify can prevent significant harm to you and your organization.
For more information and cyber security tips about phishing attacks, please feel free to contact us at marketing@ctlink.com.ph.
Remember that staying informed about phishing attacks and their prevention is vital to your online security. Stay vigilant and share these tips with your friends and colleagues to help protect everyone from potential threats.