It has recently been reported and come to the attention of Microsoft of two critical zero-day vulnerabilities that affect Microsoft Exchange Server 2013, Exchange Server 2016, and Exchange Server 2019. The first one, identified as CVE-2022-41040, is a server-side request forgery (SSRF) vulnerability, while the second one, identified as CVE-2022-41082, allows remote code execution (RCE) when Exchange PowerShell is accessible to the attacker.
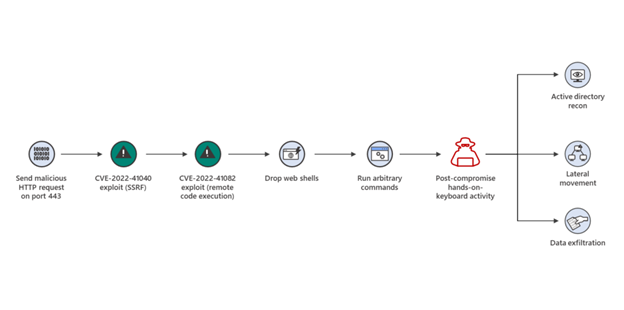
CVE-2022-41040 can enable an authenticated attacker to remotely trigger CVE-2022-41082. However, authenticated access to the vulnerable Exchange Server is necessary to successfully exploit either vulnerability, and they can be used separately.
Unfortunately, there is evidence that there are currently active attacks using these vulnerabilities as of today. As of today, Microsoft is still working on a patch/update to fix this vulnerability. They have provided a few ways to mitigate the issue in the meantime. We strongly suggest that you take the following steps to mitigate the threat
Known Mitigation
Firstly, if you are an Exchange Online customer, you do no need to take any action as Microsoft security already has you covered. For those using Microsoft Exchange Server 2013, Exchange Server 2016, and Exchange Server 2019, you may try the 3 options below:
Option 1:
For customers who have the Exchange Emergency Mitigation Service (EEMS) enabled, Microsoft released the URL Rewrite mitigation for Exchange Server 2016 and Exchange Server 2019. The mitigation will be enabled automatically.
Option 2:
Microsoft created the following script for the URL Rewrite mitigation steps. https://aka.ms/EOMTv2
Option 3:
Customers follow the steps found here for the third option for mitigation
You may read more about the different preparations your business can take here. You may also consult with us directly by contacting us at marketing@ctlink.com.ph.

