Service Framework for the Implementation of Email Security

Email remains a vital communication tool for businesses, especially for remote teams who rely on it to stay connected with clients and colleagues. While enhancing email infrastructure to improve user experience is important, ensuring robust email security is even more critical.
While training your staff to recognize and respond to Business Email Compromise (BEC) attacks is essential, human error is always a possibility. Even one wrong click can expose your business to risks. Attackers are also increasingly mimicking the writing styles of colleagues, making their emails more convincing. This is where our Email Security Implementation Services come in.
At CT Link Systems, Inc., we simplify the process of implementing strong email security. We collaborate with your team to establish security policies that protect your organization, all while maintaining a seamless user experience. Our service framework ensures that your email security is comprehensive and easy to manage.
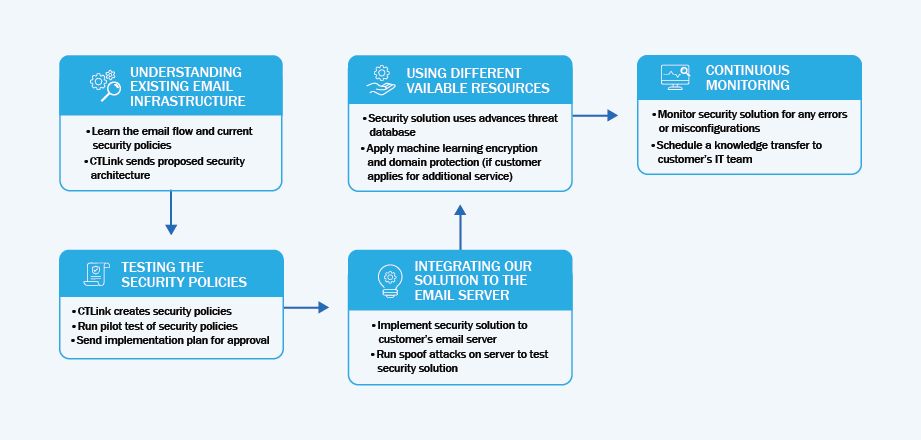

Understanding Existing Email Infrastructure
We first take a look at your current email infrastructure. Learning how you email flow works is essential in making a better security infrastructure. We send our proposed security architecture design to your team after this step.

Testing the Security Policies
We run a pilot test for the security policies before implementation. This is to ensure we keep errors and misconfigurations at a minimum during the live application.

Integrating Our Solution to the Email Server
Once live, we do a series of spoof attacks to test the security solution. We do this to make sure that the security solution is running as intended.

Using Different available resources
The security solution makes use of a continuously updated threat database. Making use of this database ensures that the solution stays relevant against emerging threats. Our solution also has the option for encryption and machine learning. This is to help lessen data loss in your business.
Another thing to consider is the risk of fake domains. Social engineered attacks are becoming more common and harder to spot. With our Email Domain Protection, you can better protect your users from these attacks.

Continuous Monitoring
The last step is to continuously monitor the live solution. Once everything is running as planned, we start the knowledge transfer to your team.
If you are interested in learning more about our services, contact us by filling in the form here. We would be glad to go into further detail with your team by having one of our team members reach out!
By clicking “Submit,” you agree to our Privacy Policy and consent to the collection and use of your personal information as described therein.
