Prevent Data Loss from Remote Endpoints and SaaS Apps with Unitrends Cloud Backup

Working from home is now the norm when it comes to business. However, this now makes data loss more common as devices are now outside your network perimeter. Traditional backup solutions require your devices to be connected to your network for it to backup your files, so every day those endpoints are not in the […]
Protecting your Data: 4 Key Reasons on Why You Should Have a Backup Solution

Data is something all businesses would agree is their most important asset, this is why they take multiple steps to ensure its security. However, when it comes to data protection, most companies are lax in its measures in the Philippines. This is alarming as data loss is not as uncommon to businesses as most seem […]
Finance: Adding Business Continuity to your Bottom Line to Help Data Resiliency
Financial firms have the task of making sure that their clients are making the most of their fiscal decisions. From services such as accounting, hedge fund management, and stock investments, your clients put their trust in you to handle their funds and ensure confidentiality. Once that trust is gone, you will most likely lose that […]
5 Data Protection Requirements in Healthcare That Unitrends Can Help with
When it comes to business continuity, the healthcare industry faces many unique requirements and challenges. With the need of 24 hours, 7 days a week and 365 days availability, and the need to safeguard the content of their electronic health records (EHRs), it can be a hard task to fulfill while still keeping within a […]
AIP Scanner: Automating Data Protection for Your Philippine Business
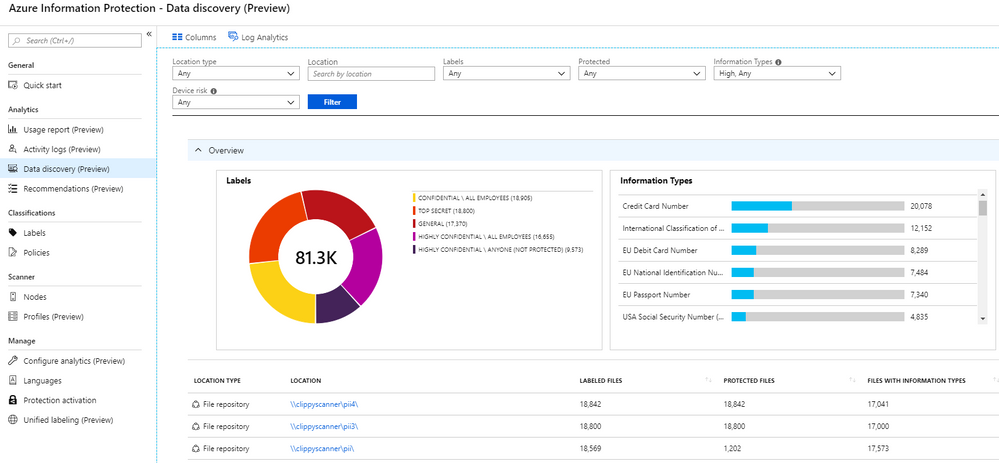
Organizations these days have large amounts of unstructured data just being left alone in their on-premises data repositories and SharePoint libraries. With the amount of data usually amounting to terabytes (or even Petabytes in some cases), it can seem like a daunting task which can take long hours to accomplish. However, with the help of […]
Ransomware Hits Florida Town Government, Costs them $500,000 in Ransom
No matter how big or small your organization is, security is always something that should be considered when it comes to securing your business data. This is especially so if you are mostly handling confidential data such as data from customers. Unfortunately, a town in Florida learned this lesson the hard way as they were […]
