4 Benefits Of Using Azure Files

What are the benefits of using Azure files? Convenience and flexibility Fast access to cloud files Business continuity Fully managed by the service provider Azure Files is a simple and secure cloud file share solution for your business. One of its benefits is the Azure File Sync, which allows you to synchronize your corporate data […]
5 Industries That Will Benefit From Microsoft Azure

What are the industries that will benefit from Microsoft Azure? Manufacturing Healthcare Financial Services Retail and E-commerce Government Some companies look for minimal hardware onsite while others look for hybrid cloud solutions. From additional storage, data security, and more — different industries have varying needs and challenges that need to be solved. The good news […]
5 Benefits Of Using Microsoft Azure For Your Philippine Business

What are the benefits of Microsoft Azure for your business? Hybrid cloud computing support Secure and reliable data storage Opportunity to scale on demand Cost-effectiveness Designed for different types of businesses Microsoft Azure is one of the leading cloud infrastructure platforms available today. It has numerous benefits for organizations such as the ability to […]
What Is Hybrid Cloud Computing?

What is hybrid cloud computing? A combination of public and private cloud Has multiple benefits for an organization Offers enhanced security for companies The go-to solution for many businesses A public cloud provides plenty of benefits for organizations, but some companies still have apprehensions when moving all their workloads to this platform. The good […]
Protect Confidential Data outside the office with Microsoft AIP!

Data is the cornerstone of a business; this is why security is a major factor in any IT environment. However, security does not safeguard your data once it leaves the network perimeter, whether it was shared within or outside the network. Many companies are aware of this and are now looking into ways to solve […]
Keep your Data Safe Anywhere with Microsoft Azure Information Protection
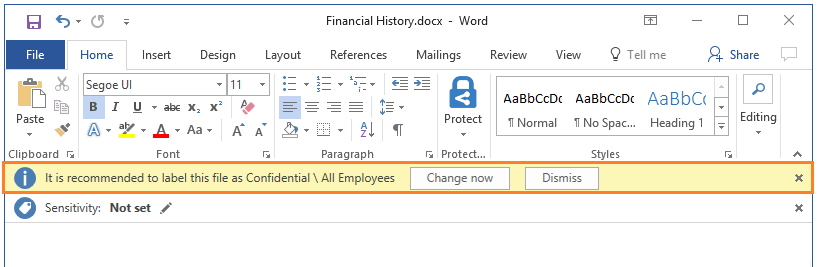
With the convenience of the internet and the evolving application market, company data is moving through different channels at a faster rate than possible before. This makes it easier for businesses to better serve the clients while also improving their operations. However, this also means that your data may be out there unprotected and used […]
