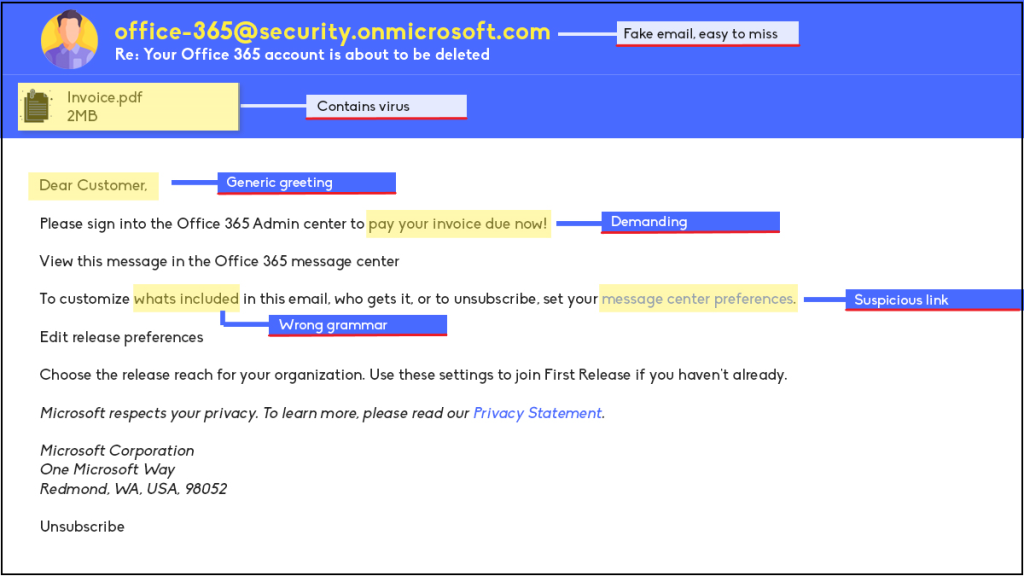
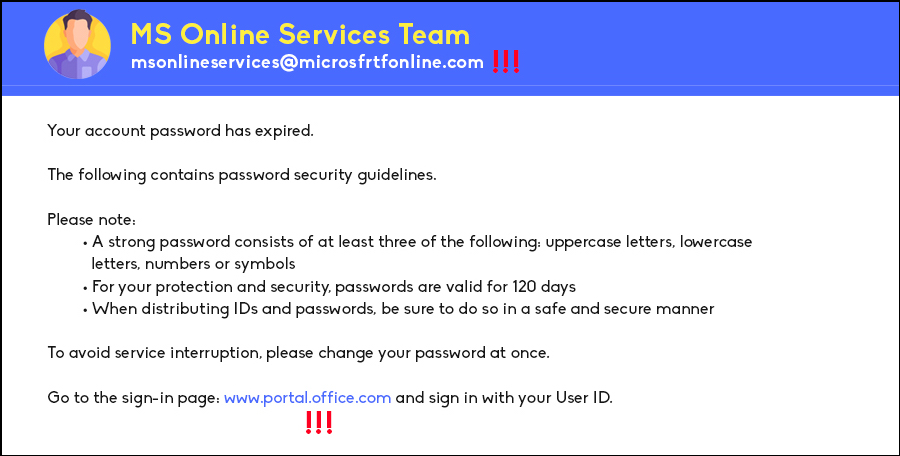
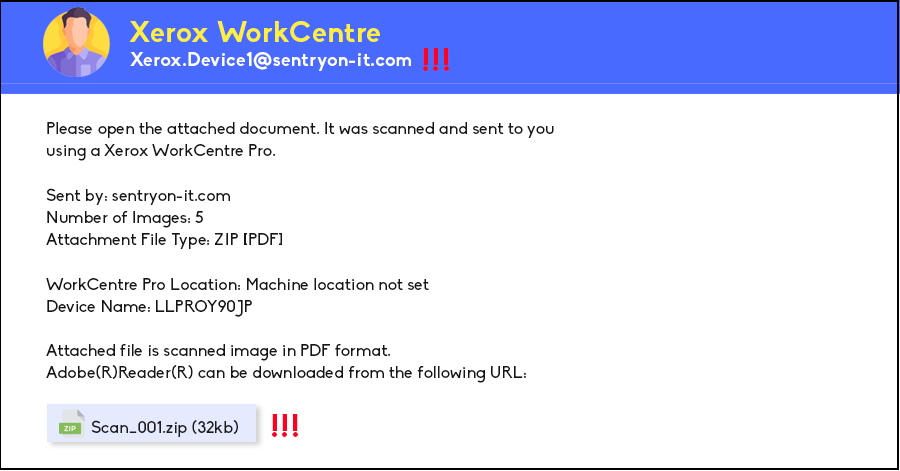
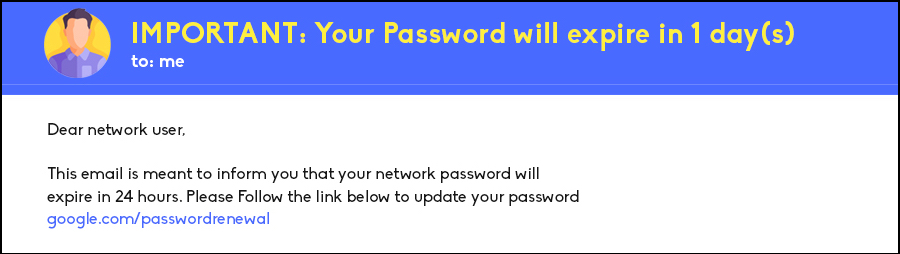
Quishing may not be a term many in the Philippines are familiar with, however, it is closely related to another well-known attack that businesses should be familiar with, Phishing. Phishing, as we are familiar with, is an attack in which tries to extract sensitive information from their victims by masquerading as a trusted entity. They then direct their victims into a spoofed website that mimics the actual login pages to then extract credentials or sensitive information.
Quishing on the other hand, is a type of phishing but how they get users to access malicious links are via quick response code better known as a QR code.
What is Quishing?
As stated above, Quishing is a type of Phishing attack in which attackers, posing as legitimate verified companies, send a QR code in place of a link. There are many reasons as to why Quishing is a very effective strategy for attackers. Firstly, many victims of these attacks are unaware that attacks like these are happening. Many potential targets are aware of Phishing attacks using URLs and many are cautious already of it. However, this is not the case for Quishing, they take advantage of user carelessness when it comes to QR code scanning.
Another reason why this attack is effective is that it can bypass security measures of companies by using a QR code instead of links. Many security solutions have an extensive database when it comes to malicious URLs. QR codes can bypass this security measure due to the nature that links are embedded into the image, allowing the URL to slip through.
A big factor to consider as well is that QR code scanning is usually done through mobile devices. These endpoints are usually far less protected than company endpoints which have many layers of protection. This makes it much easier for attackers to steal credentials or even access company resources via the compromised endpoint.
What Can Philippine Businesses Do To Mitigate Quishing Risks?
In the Philippines, QR codes are becoming more of a common thing when it comes to transactions. This shows that we are progressing when it comes to customer convenience and experience. However, this also can dull the senses when it comes to safety as it becomes more ingrained in our habits. Just like Phishing, the best way to mitigate risks of Quishing is through user education and awareness. Below are a few security practices businesses should impart to their employees:
Beware of QR Codes: Never scan a QR code if it comes from an unknown or untrusted source.
Verify via a Separate Channel: If you receive a QR code from a trusted source through email, take an extra step to confirm its legitimacy. Reach out to the sender through a different means like text message or a phone call to make sure they intended to send it.
Watch for Red Flags: Phishing attempts often create a sense of urgency or appeal to your emotions. Be cautious if a message makes you feel rushed or plays on your sympathies or fears.
Check QR Code Previews: Before opening a QR code link, inspect the URL it leads to. Make sure it looks legitimate, uses “HTTPS” for secure connections, doesn’t have obvious typos or strange characters, and is from a trusted domain. Avoid clicking on unfamiliar or shortened links.
Guard Your Personal Information: If a QR code directs you to a website asking for personal information, login credentials, or payment details, be extremely cautious. Legitimate sources typically don’t ask for this information through QR codes.
Password Hygiene: Always practice good password habits. Change your email password regularly, and never use the same password for multiple accounts.
Philippine Business Security Best Practices
In addition to educating users, organizations should consider implementing these security measures to defend against various types of phishing attacks and minimize the impact if one occurs:
Allowlisting and Blocklisting: Maintain lists of trusted and untrusted sources to control access to specific websites and content.
Antispam Filters: Employ filters that help identify and block phishing emails before they reach users’ inboxes.
Strong Email Security Policies: Establish and enforce policies that govern email usage and security practices within your organization.
Strong Password Policies: Ensure that employees use strong, unique passwords and consider implementing password management solutions.
Multifactor Authentication: Require users to provide multiple forms of verification (like a password and a unique code sent to their phone) when accessing sensitive information.
Antimalware Software: Install and regularly update antivirus and antimalware software to detect and mitigate threats.
Email Security Gateways: Utilize email security gateways to filter out malicious content and attachments from incoming emails.
Threat Intelligence Services: Stay informed about the latest threats by subscribing to threat intelligence services, which provide insights into emerging risks and vulnerabilities.
To learn more about how to better secure your business against Quishing and other modern Phishing attack strategies, contact us at marketing@ctlink.com.ph today!