The past few years have been a rollercoaster of change for the security landscape. The global pandemic caught many companies off guard due to how fast they needed to adapt to a remote work environment. This allowed threat actors to use a variety of attacks, old and new, to exploit vulnerabilities in security during their transition. However, now that we are slowly emerging from the global pandemic and slowly are slowly returning to the office, can we still say the threat landscape is the same or is there a new trend slowly emerging?
Now that we have passed the halfway point of 2022, it would be a good time to reflect and understand the current threat landscape to better prepare for the end of 2022 and the years after. Let’s take a look at the data provided by Trend Micro’s latest cybersecurity report for the midyear of 2022.
MaaS and RaaS on the Rise

Earlier this year, we saw the rise of malware-as-a-service (MaaS) and ransomware-as-a-service (RaaS). MaaS was propagated through the use of the EMOTET infrastructure that made it easier to distribute. This shows that even if EMOTET was dismantled in 2021, threat actors still use it to deploy other ransomware families to EMOTET-compromised systems.
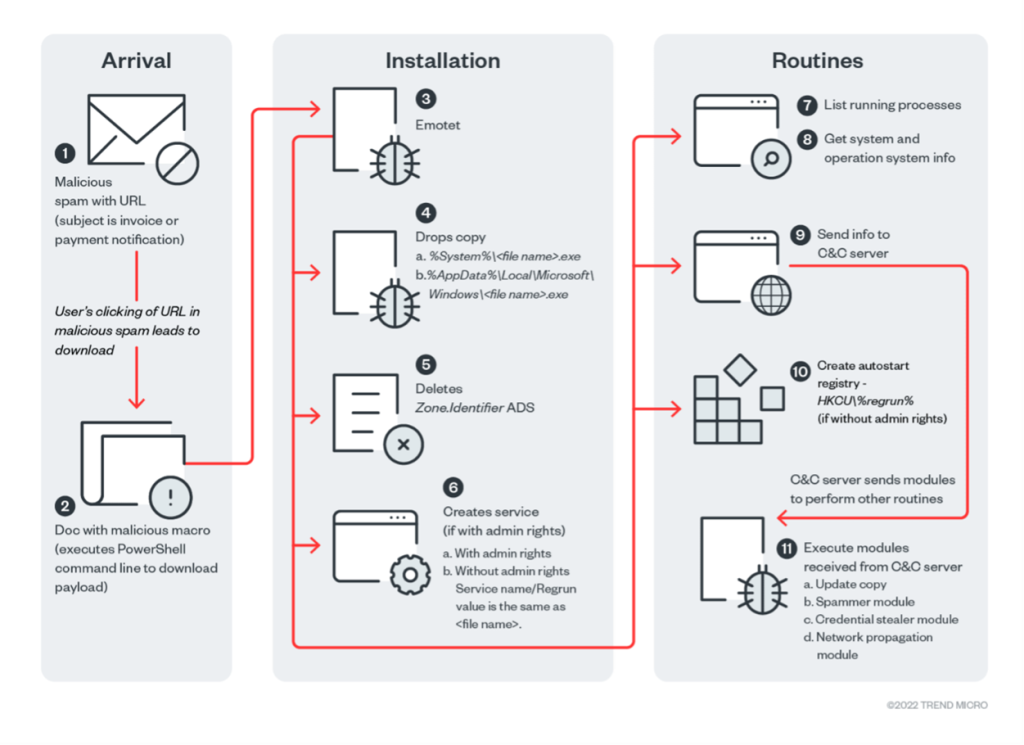
EMOTET Attack Structure
According to Trend Micro data from its Smart Protection Network (SPN) platform, EMOTET detections have soared in the first six months of 2022. The number of detections in 1H 2021 was recorded at 13,811 while in 1H 2022 it has jumped to 148,701.
RaaS on the other hand, has grown due to it’s ease of use. RaaS is available to any would be criminal organization who can either purchase the infrastructure outright or can rent it out. It also does not need any technical knowledge to run a sophisticated attack which makes it even simpler to use. Trend Micro has detected that there are around 57 active RaaS and extortion groups and almost 1,205 victim organizations based on data they have collected throughout the 1H of 2022. They use mostly ransomware such as Lockbit, Conti, and BlackCat which has been detected from Trend’s SPN network.
Cloud Misconfiguration and Cryptocurrency-mining

Cloud-based containers have become integral into the digital transformation strategies of many organizations. However, due to its tendency to be misconfigured, it has become a big target for threat actors. According to a survey from Red Hat in May 2022, out of 300 participants who took the survey, 53% of them have answered that they have detected a misconfiguration in their containers and/or Kubernetes deployment. An independent investigation from Trend into Kubernetes clusters has shown that there are over 243,000 exposed clusters via Shodan that can be seen publicly. Some of these nodes, around 600, came back with a “200 – OK” notification, meaning attackers are free to exploit them and install and run malicious programs on the kubelet API.
Another emerging threat to come recently has been threat actors who steal cyptocurrency mining capabilities from their victims’ resources. There have been five prominent threat actor groups that Trend Micro has been able to identify.
- Outlaw – Primarily targets internet-of-things (IoT) devices and Linux cloud servers by exploiting known vulnerabilities or performing brute-force Secure Shell Protocol (SSH) attacks.
- TeamTNT – One of the most technically proficient threat actors focused on cryptocurrency mining.
- Kinsing – Known for quickly abusing new exploits (including the Log4Shell vulnerability) in a short period.
- 8220 – Known for exploiting Oracle WebLogic vulnerabilities.
- Kek Security – a relatively new group that uses sophisticated techniques and integrates new exploits in its attacks.
Threats are always evolving and adapting to situations within the cyberspace. This is why businesses should always work closely with security vendors to be able to stay up to date with the latest security trends. Consulting with partners like us from CT Link or even security solution vendors like Trend Micro is one way to keep ahead of the new threats that may come in the latter part of 2022 and beyond.
To learn more about the latest in the security trends or even to find someone to help improve your current security measures, please email us at marketing@ctlink.com.ph.