Business Email Compromise (BEC) Schemes
In the past few years, millions of dollars have been lost to fraudsters and scammers. However, not all have been lost through malware attacks such as ransomware. Business email compromise (BEC) schemes are sophisticated attacks focused mostly on companies who do wireless transfers frequently. The FBI have estimated that nearly $750 million dollars have been lost to this type of schemes and affected more than 7,000 people between October 2013 and August 2015. Below are a few versions of the scheme:
The Bogus Invoice Scheme
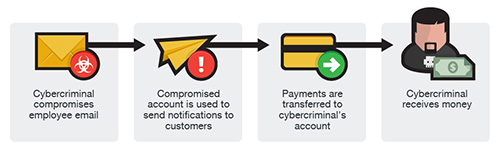
Referred to as “The Bogus Invoice Scheme”, “The Supplier Swindle”, and “Invoice Modification Scheme”. This scam is usually done by using the name of established partners of the business, they impersonate being an employee of the established partner while asking for wire funds for invoice payments to their fraudulent account by using a spoofed email, telephone, or facsimile.
CEO Fraud
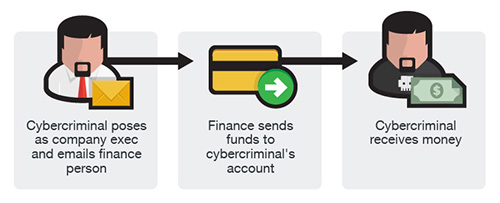
Also referred to as “CEO Fraud”, “Business Executive Scam”, “Masquerading”, and “Financial Industry Wire Frauds”. The scammers impersonate high-level executives (CFO, CEO, CTO, etc.), lawyers, or other types of legal representatives while urging the victim that they are handling confidential and time-sensitive matters then pressuring the victim into wire transferring funds to a separate account which they control.
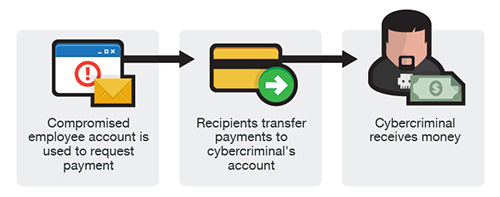
Account Compromise
- Carefully scrutinize all emails. Be wary of irregular emails that are sent from C-suite executives, as they are used to trick employees into acting with urgency. Review emails that request transfer of funds to determine if the requests are irregular.
- Educate and train employees. While employees are a company’s biggest asset, they’re also usually its weakest link when it comes to security. Commit to training employees according to the company’s best practices. Remind them that adhering to company policies is one thing, but developing good security habits is another.
- Verify any changes in vendor payment location by using a secondary sign-off by company personnel.
- Stay updated on your customers’ habits including the details, and reasons behind payments.
- Confirm requests for transfer of funds when using phone verification as part of two-factor authentication, use known familiar numbers, not the details provided in the email requests.
To learn more about BEC attacks, you can read a more in-depth article from our partner’s, Trend Micro, informative article here. If you have inquiries that you would like answered about this topic, you can also contact us at 893-9515 and we will be happy to help!
Prevention tips
This scam usually involves compromising an email of a role-specific employees (usually HR) in the victim’s company, then using the said email to gather identifiable information of other employees and executives which is later used as a jump-off point for more damaging BEC attacks to the company later on.
Below are some quick prevention tips on how you can avoid these types of attacks:
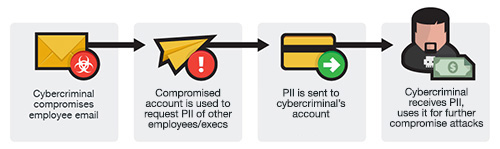
Data Theft
In this scam, an email account of an employee is hacked and then used to make requests for invoice payments to fraudster-controlled bank accounts. Messages are sent to multiple vendors identified from the employee’s contact list.
