Security Advisory: PlunderVolt, A new Vulnerability found in Intel Processors
Academics from three universities across Europe have disclosed today a new attack that impacts the integrity of data stored inside Intel SGX, a highly-secured area of Intel CPUs. It was reported by three academics from three different universities across Europe that a new attack was re that affects the integrity of data stored in the […]
Cloud Security: The Shared Responsibility Model
Have you ever asked yourself what the biggest threats are in the cloud? The answer may not be what you’d expect it to be. Rather than big named malware or cyber attacks, the biggest risk in the cloud happens due to service misconfigurations. Despite the cloud’s clear operating model, teams continue to make simple mistakes […]
Ransomware Hits Florida Town Government, Costs them $500,000 in Ransom
No matter how big or small your organization is, security is always something that should be considered when it comes to securing your business data. This is especially so if you are mostly handling confidential data such as data from customers. Unfortunately, a town in Florida learned this lesson the hard way as they were […]
Security Advisory: Microsoft Alerts to Patch for BlueKeep Vulnerability
In case you didn’t hear, another big vulnerability was reported by Microsoft on May 14, 2019 known as “BlueKeep” which takes advantage vulnerabilities of Remote Desktop Services (RDS), Remote Code Execution (RCE), and Remote Desktop Protocol (RDP). However, BlueKeep only affects older version of Windows, so users of Windows 10 and 8 can rest easy. […]
Security Vulnerabilities: A Closer Look at a Criminal’s View of your Business Systems
You may be hearing more and more these days of new security vulnerabilities being discovered in the news and may be wondering what exactly it may imply? Simply, a vulnerability represents the ideal opportunity for cyber criminals to infiltrate your system to compromise your data or to perform data theft. According to current data now, […]
Managed Detection and Response: Helping to Fill in Gaps of Business Security
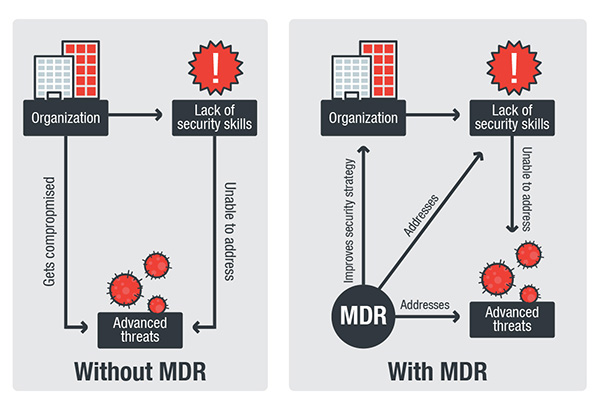
Managed detection and response (MDR) is an outsourced service that provides organizations with threat hunting service and responds to threats once they are discovered. What sets it apart from other security services is the human element in which security providers provide access to their security resources such as their researchers and engineers who will now […]
