Before the Covid-19 pandemic, many companies did not provide their workforce with client VPN access due to the concern on the security of data. However, most companies were caught flat-footed when the government suddenly announced the Enhanced Community Quarantine (ECQ). This forced many companies to adopt a short-term remote access solution by enabling the Client VPN feature that came with their firewalls. As the quarantine extended, many have come to realize that their Client VPN firewall feature would not be enough as a long-term solution.

Holes in traditional VPN Firewall Solutions
Existing Firewall solutions were used by majority of companies here as a band-aid fix to their BCP/WFH needs during this crisis. They quickly realized that after enabling this feature, that their firewall was not equipped to accommodate the large amount of client VPN users. This is either due to the limitation on the number of concurrent users, or the hardware has a limited throughput for VPN users leading to a poor user experience.
Another concern with traditional firewall-based VPN is that it provides full access to remote users with minimal control and visibility on what the users are doing, which leaves the IT team unaware if most users are accessing the corporate network with security compliant devices. In fact, with an increase of varying location, time of access, and device used, it makes it even harder to spot malicious activity. This can increase the chances of your company from suffering a data breach or experience data leakage.
In fact, even malware residing on the user’s home PCs can traverse over the VPN and arrive to your corporate network if not properly secured. VPNs are used more to encrypt your data so that outsiders are not able to view your data or hijack it. It does not mean that infected files from unsecured endpoints will be scanned through a VPN.
Zero Trust Secure Remote Access Solutions
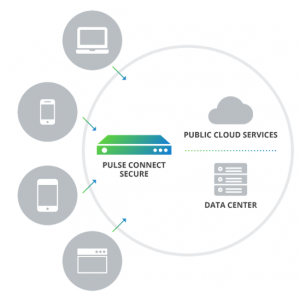
Companies need to fortify their security capabilities to prevent and contain cyberattacks and data leakage. With the help of more advanced remote access solutions like Pulse Connect Secure, your company can solve beyond the traditional dilemmas while ensuring future scalability.
With Pulse Connect Secure, it always enforces the strategy of verification before trust to ensure that only authenticated users with compliant devices can connect to authorized applications and corporate resources at any time, from any location, over any network. By always verifying, it is ensured that:
- The user trying to access the network is who they claim to be to keep the wrong people out, through a multi-factor authentication in place
- The device used to connect to the network is an authorized device (i.e. company-issued laptop) or has met the specific corporate security requirements to decrease the possibility of malware infiltration and data loss
- Users can only access authorized resources based on their roles to limit access to confidential information and reduce chances of data leakage
To learn more about secure remote access solutions, send an email to rcruz@www.ctlink.com.ph or contact your CT Link Account manager today!

