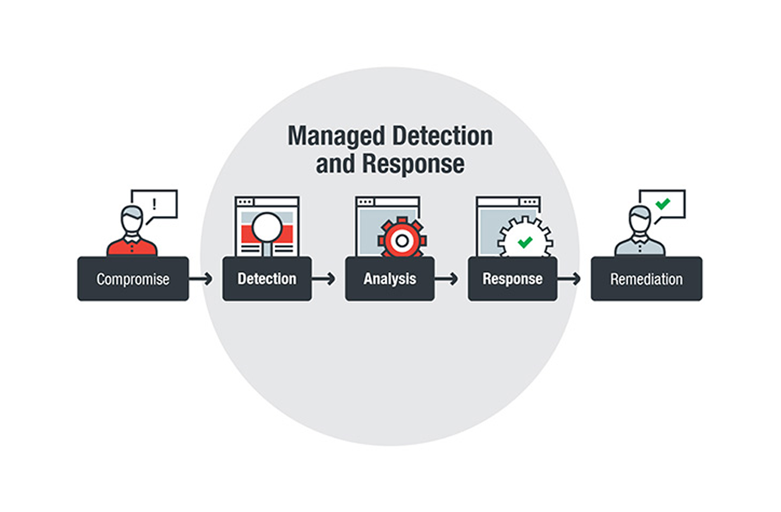
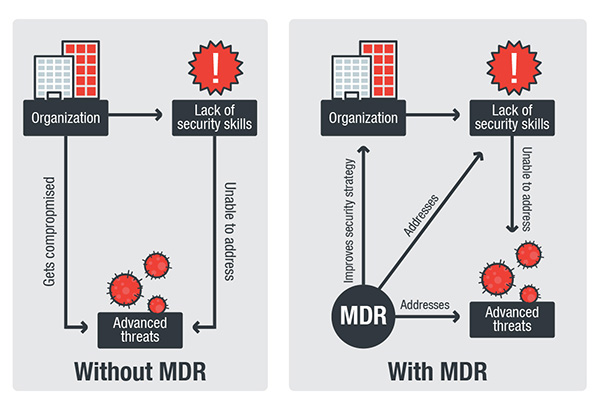
Are you sure you are securing your SAP environment properly?
With the sensitive data stored in most SAP systems (HR, financials, and even more important, customer data), it would not be an exaggeration to say that it would be the main priority of attacks of cyber criminals. This doesn’t mean that SAP does not prioritize security, this just means that security solutions have been continuously improving with the help of 3rd party enhancements. In partnership with SAP, there are security solution partners such Trend Micro that ensure that enterprises are secure from attacks such as malware, denial-of-service attacks, cross-site scripting and other advance and targeted attacks.
So if you aren’t sure if you are properly securing your SAP environment, you can refer to this security question checklist below:
What are my security risks? Are you improving your ability to respond to customer feedback by moving customer applications to the cloud? Are you improving supply chain efficiency by opening an application to provide more visibility or communication with partners?
With how business-critical applications are now web accessible, cyber criminals now have more entry points in which they can exploit vulnerabilities in operating systems, web servers and even the business-critical application itself. Although vendors release patches to fix these vulnerabilities, if they are not implemented on a timely basis, the system will still be at risk within those transition points.
Does my security integrate with my SAP environment?
You also need to consider whether your security can integrate well with your native SAP security. SAP provides capabilities like the SAP Virus Scan Interface (VSI) as part of SAP NetWeaver ® to allow certified third parties, like Trend Micro, to augment native security capabilities.
What are the security requirements for my environment?
Cloud and virtual environments each introduce unique requirements for security. Understanding how your security solution is optimized for those environments is critical to make sure you can easily manage security and reap the expect cost, performance and agility benefits.
If you have any further inquiries on how you can better secure your SAP environment, you may call us at 893-9515 and we would be happy to help!