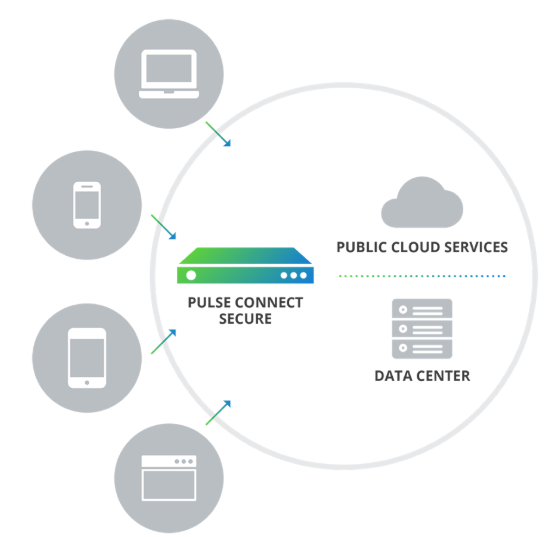
Digital transformation is changing the business norms. Access and connectivity are becoming more flexible as devices, users, applications, and infrastructure adapt to a new era of hyper-connectivity. This has prompted enterprises to consider how to secure access for their users and applications while managing cybersecurity risks in a network with little to no boundaries. This is where Zero Trust solutions like Pulse Zero Trust Access (PZTA) comes into play.
The PZTA platform enables diverse users from any location to access public, private, and multi-cloud applications as well as data center resources securely while staying user friendly. Be it a hybrid cloud or pure cloud strategy, PZTA can help organizations enhance their security, productivity, and compliance while also improving administrative and user experience.
Below are a few key areas in which PZTA can help improve:
On-premises, SaaS and Hybrid Cloud Applications
PZTA allows you to have Zero Trust Secure access remotely or on-site to your corporate applications whether they are located in your network perimeter or in the cloud (private or public). Users and devices are authenticated continuously while maintaining secure entry points for your network and user device through the use of encryption channels.
Keeping user and application traffic
within the corporate network
Organizations can be confident when users from any location access any application using any device. All user traffic is directed to PZTA which acts as a middleman where user requests are fulfilled by PZTA accessing data from the corporate network on their behalf. Since data are not accessed directly by users, this lowers the area of attack of compromised accounts and devices.

Difficulty of managing
resources in the cloud
The PZTA cloud-based service emulates the same access and management experience as an on-prem solution. This means that you can enable the same level of visibility, compliance, enforcement, and analytics as you would in an on-prem solution.
Visibility, Enforcement and Compliance Reporting
PZTA provides a single pane-of-glass visibility of all users connecting to your network, regardless of the location of the user, application, or resource.
Visibility gaps
From the PZTA dashboard, administrators can get holistic visibility of users, devices, infrastructure, and applications as all access is authenticated and authorized by it. These are also logged in the dashboard for reporting and auditing purposes.

Ensuring user endpoint compliance
PZTA first goes through a set of policies during authentication to see if devices trying to access the corporate network are compliant. Users can then follow pre-defined remediation given set by the administrators so that they may access the network.

Measuring users’ risk factors
User activities are measured and given a “risk score” based on users’ behavioral patterns. Stricter authentication or restrictions can be dynamically applied to verify the user’s identity once there is behavior outside the norm detected. This continuous anomaly and malicious activity detection is used to ensure the network’s security.
These are just a few ways in which Pulse Zero Trust Access can help companies improve their visibility and security. If you would like to learn more about Pulse Secure solutions, you may fill out the form below and we will contact you as soon as we can!